CTB Locker Ransomware Removal
CTB Locker also uses encryption techniques to encrypt users’ data and then demand ransom in order to obtain a decryption key. A common delivery method is through email attachments that may seem to be legitimate to some. These attachments contain files that will execute a download on the system and then run it’s damaging course. Another method is via driveway downloads. This occurs when a user visits an infected website and malware is downloaded and installed on the user’s system without them even knowing. Other methods include social media, malicious links, popup ads as well as others.
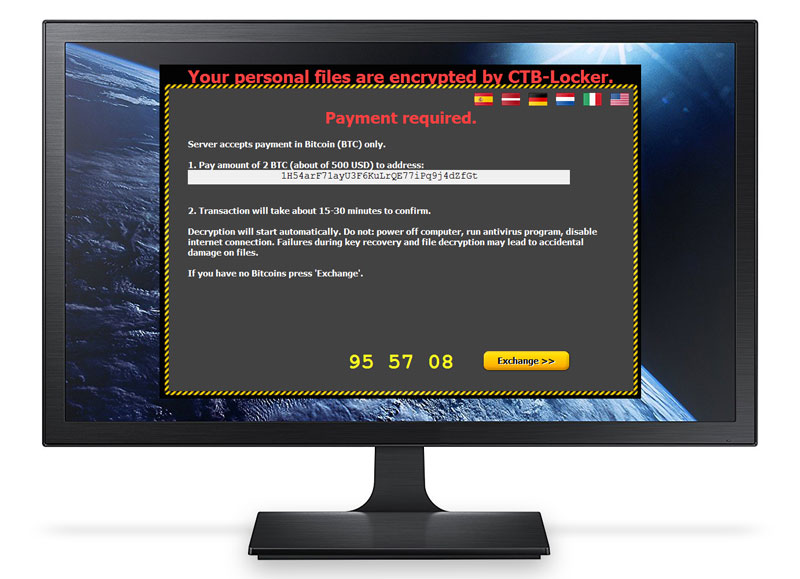
CTB differs slightly in it’s delivery and implementation of encryption and how the user may obtain the decryption key. This malware is also one of the first to encrypt actual websites demanding the site administrators pay ransom to get their sites back.
To show “good faith”, this malware will actually allow you to decrypt two files of your choice for free. Just to show that the decryption code being offered actually works. Many people fall victim to this and ultimately pay the ransom demanded simply because they are unaware of possible solutions, such as RansomRescue.
RansomRescue Advice
It is strongly advised that you do not pay any ransom demand. But instead contact RansomRescue immediately. When paying these ransoms, people and businesses are inadvertently sustaining this unscrupulous business models (yes RansomWare has become a business model!) and allowing them to flourish and continue infecting and disrupting the business world.